Common WP Security Mistakes
WordPress security is the responsibility of your users that login as well as your web developer. If someone has access to the Admin of your site or code, they are a potential threat to your site’s security integrity. Ensure that your users (including yourself) and your developer are not making simple security mistakes.
WordPress Maintenance
Mistake #1: Leaving WordPress Core, Plugins, or Themes Outdated
You have spent countless hours building your WordPress website. Now you can get back to other things that are more important. However, months go by before you log back into your site. By this time you have multiple plugins and/or themes with updates available and possibly even WordPress core itself. Since you were not expecting this to be the case, you push forward with your original purpose of logging into the website such as: posting new content, responding to comments, adding a new user, etc. You’ll update the site software later. Unfortunately, this common situation repeats itself over and over since the website already functions properly and it just does not seem to be as high priority as other tasks at the moment. In this dynamic, keeping core, plugins, and themes updated only becomes a priority once something goes wrong.
If your website is using outdated WordPress core, plugins, or themes, you are potentially exposing yourself to a security vulnerability. The easiest way to ensure your site stays up-to-date is to plan on monthly updates or pay for a service that will take care of those tasks for you.
Mistake #2: Using Plugins or Themes That Are No Longer Supported
When you are logged into the WordPress Admin, you can navigate to the Plugins page to view all of the installed plugins and see which ones need updates. If you have already taken the advice above and updated all your plugins to the latest version, good job. Unfortunately, that is only the first step.
The next step is to verify that all the plugins are still being maintained. To do this, click on the “View details” link provided for each plugin.
A popup window should appear containing the plugin profile page located on WordPress.org. The profile might have a warning box informing you that the plugin may not be compatible with your current version of WordPress. If this is the case, you may want to thoroughly test your site to ensure the plugin is working as expected. The most important part of this screen is the Last Updated date located on the right-side panel.
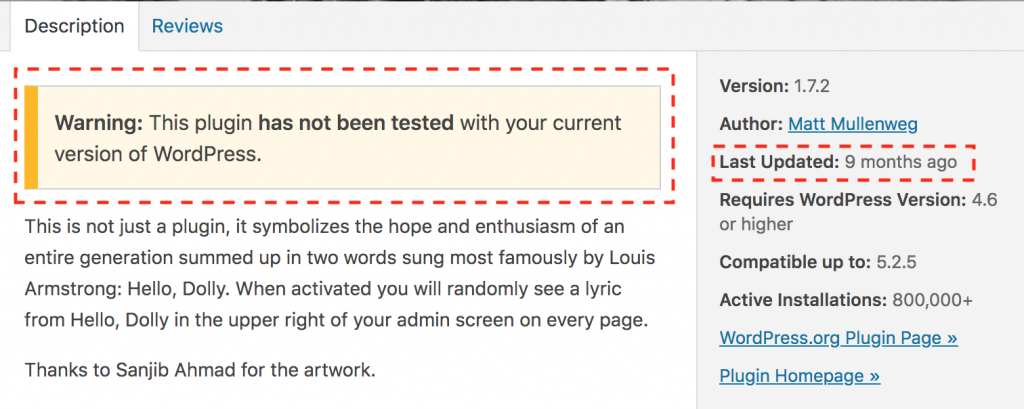
Some plugins require more frequent updates than others. Regardless of the complexity of the plugin, if the Last Updated date is 2 years ago or longer, then the plugin is likely abandoned or no longer being supported by the author.
Problem:
- Website Might Break – The plugin is at risk of breaking your website after a WordPress core update.
- Future Security Issues – Since the plugin is not receiving occasional updates, it is unlikely the author will fix any future security issues, thus placing your website at risk.
Possible Solutions:
- Find another plugin – See if there is another plugin out there that provides the same or similar functionality and use it instead.
- Delete the plugin – Determine if you really need the plugin’s functionality. If not, remove it and move on.
- Fork the plugin – If you cannot live without the plugin and have enough developer skills to take on maintaining it, then rename the plugin’s directory. Then change some of the basic details located in the main plugin file. Make sure that you change the title of the plugin to include “custom” and add yourself as the first author so that it is clear that you need to maintain it. It would also be recommended that you look through the code to ensure that you understand what it is doing and to potentially catch an obvious security issue.
- Copy the functionality into your theme – If the functionality is pretty basic and straight forward, then copy that code directly into your functions.php file in your custom or child theme and then remove the plugin.
- Contact the author and encourage them to update the plugin – This could be a waste of time as the author may not respond to your email. If the author is a company, they will be more likely to reply to your message.
As you can see, this process is not necessarily as fast one. To make things a little more manageable, plan on doing this at least once a year as part of your annual security audit process.
Mistake #3: Keeping Unused Plugins or Themes
As you go through and update your plugins, you may realize that some are not needed and disable them. If you truly do not need them, then disable and delete them. Even though a plugin or even a theme is not active, a vulnerability in the code could give an attacker the ability to write to your file system. Disabling a plugin or theme does not necessarily protect you.
Warning: If you are cleaning up themes, be sure you do not delete your parent theme.
Security Login Issues
Mistake #4: Giving Users Too Much Access
At some point you may need to give someone temporary or ongoing access to the WP Admin. A typical situation would be a freelance writer, SEO expert, or a marketing firm. Often times, website owners will give these people a new account with an Administrator role. If these users will not be installing or turning on/off plugins, then give them a lower level of access. Start with the Author role if you want to screen what gets published. If you would like to let them publish at will or edit other author’s content, then assign their user with the Editor role.
If someone insists that their user has the Administrator role, ask them why they need it. You may be able to go in and accomplish the task for them; removing their need for that level of access.
Be very selective as to whom you assign the Administrator role. The more users that have this role, the more targets a hacker has to break into your site. A good rule of thumb is to have no more than 3 accounts with the Administrator role.
Mistake #5: Multiple Users Sharing Access
Marketing firms are notorious for sharing access. If multiple people are using the same user account, it becomes impossible to figure out who did what. When multiple users share an account, it is unclear which people have access to the website. To make matters more frustrating, if two users are using the same login account and editing the site at the same time, they could actually overwrite each other work unintentionally and not realize it. A separate account will lock a page while another author is editing it; preventing data loss.
Give each user their own account and only give them the minimum access they need to accomplish their tasks.
Mistake #6: Email or Text Usernames And Passwords
This is a quick way to get your website hacked. Email is not a secure form of communication regardless of who the provider is [r]. The same goes for apps that allow you to chat. Short messaging services (SMS), aka text messaging, is old technology that is behind the curve on security and can be intercepted (SMS hijacking) [r].
The secure way to give someone access to your website, is to create them an account with their email address and send the user a notification email. The email will contain a link to allows them to set the password for their account. The link will expire after someone clicks on it for the first time.
Mistake #7: Using Predictable Login Credentials
Use a username that is uniquely yours and not generic. Do not use “admin”, “manager”, “wordpress”, “administrator”. These generic usernames are targeted everyday by hackers. To go even further, do not make your password be the same as your username. That leads me to the next topic…
Mistake #8: Using Weak Passwords
I can already hear you groaning about this one. You have likely been harassed by many websites forcing you to use strong passwords and spending the next 5 to 10 minutes of repeated failure attempting to do so. It is not fun trying to create a password that is strong and simple to remember. Avoid all that nonsense and use a service like LastPass to remember the password for you and choose the strongest and longest automatically generated passwords. If the worst case scenario happens and you cannot remember your password due to not having immediate access to LastPass at that very moment, then just reset it using your email to recover the account. Just remember to make the new password long and strong (save it in LastPass).
Mistake #9: Using passwords longer than you should
Passwords are similar to New Year’s resolutions. You are supposed to make new ones every year. Any security consultant worth their salt will tell you every 3 months. Unfortunately, that becomes a full-time job if you were to implement that methodology with every user account you have out there on the internet. The best advice I can give regarding changing passwords is this: Ask yourself how important is your website? The more revenue your website brings in monthly, the more damaging it would be to get your account hacked.
Try adopting a more frequent password changing schedule for accounts that have Administrator roles and a less frequent schedule for lower access roles. This makes the situation more reasonable, otherwise you will find yourself never changing your passwords.
Mistake #10: Recycling Passwords
Reduce, reuse, and recycle, but not your passwords! You should never use a password that you have used before. I know how frustrating it is to hear this, but it is solid advice. If one of your accounts is hacked, your information will immediately be used to attempt to login to other accounts that you have. If all your accounts use unique passwords, then the security breach is isolated to one account instead of multiple (or all) accounts.
Just randomly generate a new long password and use LastPass to remember your passwords for you. Problem solved and frustrations gone.
Mistake #11: Stale Accounts
As time goes on, you may need to add user accounts for various people such as content writers, web designers, web developers, marketing agencies, and the list goes on. It is imperative to provide these users the proper relative access that is appropriate for their purpose. It is even more important to remove their access, if they no longer serve an active purpose for the site.
When an account is no longer used on a website, becomes stale, the password does not get changed and hackers can continually try their hand at guessing the password. Moreover, if the username and password of the stale account has been used on other websites, the stale account becomes a ticking “time bomb” once any of the other websites encounter a database security breach. This scenario places your website at risk of someone gaining unauthorized access.
Finding the Stale User Accounts
How do you tell if an account has not been used in a long time? There are WordPress plugins that can help you see additional information about the user such as the Created Date, Password Updated, and Last Login on the Users admin screen. This type of information can easily help you identify if the password needs to be changed or if the user account is stale altogether.
How to Fix Stale Accounts
Once you have identified a stale account do the following:
- Change the user’s role to “Subscriber” only. This will reduce the level of access the user has and limit the damage a hacker could possibly do if they are able to gain unauthorized access.
- Change the password. If the account is stale, it is likely the password is as well. Change the password to a long random string. If the user needs access and does not have the new password, they can simply reset their password on from the login screen.
- Contact the user. Email the user and ask them if they need this account. The user’s email should be associated with the account.
- Delete the account. If you have determined that the account is no longer needed, then get rid of it.
Notice: Worst Case Scenario: If you find out that the account is needed after you have removed it, then you can just add a new account to give the user access again.
Mistake #12: XML-RPC enabled
XML-RPC is some cool technology that allows you to remotely publish content on your site without visiting the website in your browser. Unfortunately, it comes with some serious security risks such as being susceptible to brute-force login attacks. This method of publishing was more commonly used before smartphones were as fast and smart as they are today. Today, this method has become more or less obsolete. Use a security plugin to disable this feature. It will not only help protect you from brute-force attacks, it will reduce a serious load on your hosting server.
Best Practices
Mistake #13: Assuming You Do Not Need A Security Plugin
As mentioned in the previous mistakes above, use a security plugin. You could grab some snippets of code from various websites to piecemeal your security solution into your custom or child theme. Unfortunately, WordPress is continually changing and that means if you are manually adding snippets of code into your theme, then you will be responsible to maintain that. The likelihood of you or another developer keeping up with the security standards and code compatibility is very low. If you use an actively support security plugin, then you can expect that the author will continue to release new versions that have been tested with the latest versions of WordPress.
Security plugins are not created equal as some are more robust than others. Nevertheless, a security plugin is better than no security plugin. Regardless of the brand name of WordPress security plugin; choose one and only one that meets the needs of your website. Multiple security plugins running at the same time will often overlap in functionality and bog down your website unnecessarily.
Warning: Multiple security plugins running at the same time will possibly break your website in not so obvious ways leaving your site dysfunctional and more vulnerable to an attack.